| FTP Issues and Solutions | ||||||||||||||
|
Noah Davids FTP issues seem to be cropping up more and more often. This article will discuss several of the more common ones and present a possible solution. Firewalls and connection problems:Error messages reported by client applications are as varied as the clients themselves, but the symptoms are always the same. You can make a connection to the server and login, but you cannot transfer any files or list a directory. To understand the problem, you have to understand how FTP manages its connections and transfers a file. Listing a directory is treated the same way as transferring a file. Just to make things difficult there are two different ways FTP can do this. In default mode (figure 1) the FTP client sends a PORT command to the server telling it the IP address and port number on which it will listen. The FTP server then makes a connection from port 20 (the FTP data port) to the IP address and port number specified in the PORT command.
With passive mode (figure 2), the client first sends a PASV command to the server telling it to enter passive mode. The server responds by listening on a new port number and sending back a response to PASV that includes the port number. The client then connects to that port number.
What does all this mean? Look at the network diagram in figure 3. Both the client and the server are protected by firewalls. The server firewall must allow packets addressed to the server's FTP control port (21) to go through, or a connection cannot be made to the server. However, the firewall generally will block incoming connection requests. Assume that the client is using the default mode. It sends a PORT command to the server, which then attempts to connect to that port. This is blocked by the client's firewall. In passive mode, the server sends a port number to the client in the PASV response message, but when the client tries to connect, its blocked by the server's firewall. Most firewalls can monitor FTP connections for PORT commands and PASV responses and open the appropriate holes in the firewall to allow the connections. Once the connection terminates, the hole is closed. However, some firewalls can't or won't do this - at least not unless configured to do so by the network administrator.
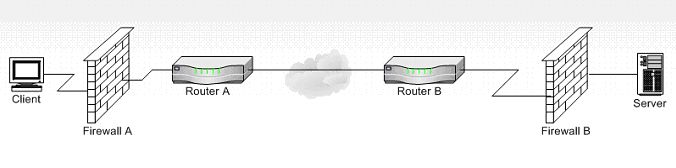 Figure 3: Example network The STCP FTP server supports passive mode starting in VOS releases 14.6.1az, 14.7.0ag, 15.0.0ac, and 15.1. The STCP FTP client supports passive mode starting in releases 14.7.2ah, 14.7.tl1.ag, 15.1.2ak, 15.1.tel.ah, 15.2 and 16. On an ftServer® system, the Microsoft® Windows® IIS environment does support passive mode, however, it's a mixed bag for the client. You can configure Internet Explorer to use passive mode. Select "Internet Options" from the Tools menu. Then on the Advanced tab scroll down about half way and check the "Use Passive FTP for firewall and DSL modem compatibility". See figure 4.
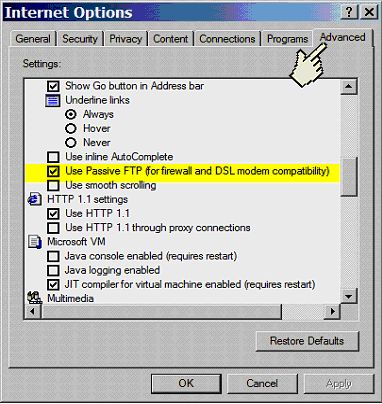 Figure 4: Configuring Internet Explorer to use passive mode However, the FTP client you can run at the command prompt does not have a way to get into passive mode. I'll end this section by explaining how to figure out the port number specified by the PORT and response to PASV messages. The format is A,B,C,D,X,Y. A,B,C,D is the IP address. Note that the octets are separated by comas not dots. The X,Y represents the port number. The actual port number is calculated as: 256 * X + Y For example, in figure 1 the client's PORT command specifies 164,152,77,50,17,253.
The server connects to port 4605 NAT/PAT and connection problems:Network Address Translation (NAT) and Port Address Translation (PAT) devices modify the IP address and/or port numbers in the IP header for all IP packets leaving the (inside) network. They keep track of the original and modified values so that when a response comes back, they can reverse the mapping. The typical reason for doing this is that the inside network has more devices i.e. IP addresses than the network has public IP addresses. The NAT/PAT devices allow you to multiplex the public IP addresses among the inside hosts. Another reason for using these devices is to delay (perhaps permanently) the readdressing of a large number of hosts. Some people also feel that these devices enhance security, since special configuration is needed to allow an outside host to initiate a connection to an inside host.That, of course, is the "feature" that prevents FTP from working. Go back to figure 3 and imagine that the firewalls are now NAT devices. In default mode, the server makes a connection back to client. But, the IP address in the PORT message is the IP address that the client thinks it has, i.e. the inside address. The server probably does not have a route to that address. In addition, the port number in the PORT message does not have a mapping in the NAT/PAT map table. If you assume passive mode, you have the same problem from the servers end. Admittedly, it is less likely that the server has a NAT/PAT device in front of it, but it is not impossible. Like firewalls, the NAT/PAT device can be configured to send connections to port 21 to an FTP server. Also like firewalls, FTP can be made to work with NAT/PAT devices. The trick is for the NAT/PAT devices to monitor traffic passing through them and add a mapping, allowing a connection to the request port number through. Unlike firewalls, NAT/PAT devices must also modify the packets to adjust the IP address to the outside IP address. Because this can change the length of the PORT or PASV response messages, NAT/PAT devices must also be able to adjust the TCP sequence numbers and checksums. This must be done not only for the PORT and PASV response messages, but for all subsequent messages in the connection. GUI interface user clients do not work:The command line version of FTP is now passé; people want to be able to drag and drop files. The simplest way to do this is with Internet Explorer; just put in the URL for the FTP server and away you go (figure 5). Unfortunately, when connecting to an STCP server, you get something that appears to be very strange (figure 6). This is because the results of the "dir" command are not Unix-like and, therefore cannot be parsed by the FTP client. You can still get a list, but you cannot do anything with it or get to any subdirectories.
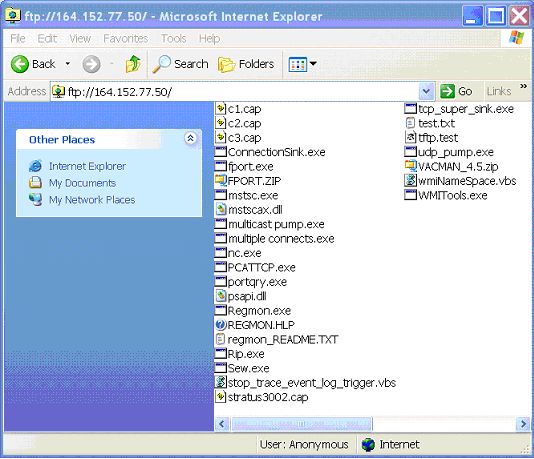 Figure 5: Internet Explorer displaying a Windows based FTP site
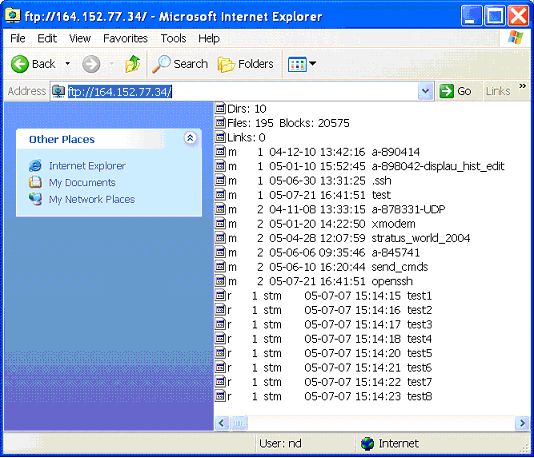 Figure 6:" Internet Explorer displaying a STCP- based FTP site There is a suggestion to change the output so it is compatible with most GUI FTP clients (sftp-9) but I don't think it will ever be accepted. One reason is that there are FTP clients that can parse STP's output, so changing it would break them. The programs that I have used in the past are TTWin (figure 7) and WS_FTP Pro (figure 8).
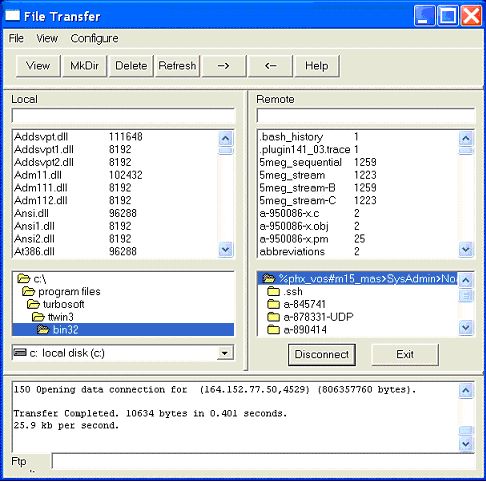 Figure 7 TTWin FTP client displaying a STCP-based FTP site
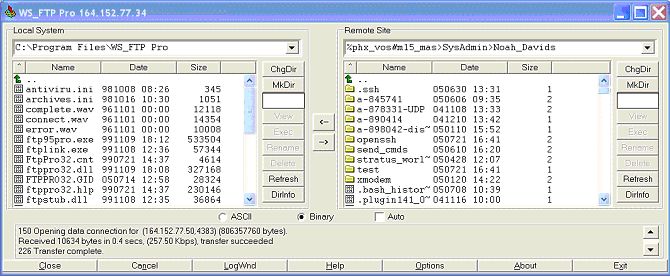 Figure 8: WS_FTP FTP client displaying a STCP-based FTP site Passwords, File, and Directory content are visible to everyone:There are two related security issues with FTP. First, anyone with an analyzer can see your password (figure 9). Second, anyone with an analyzer can see the contents of files you transfer (figure10) and the contents of any directories that you list (figure 11).
Changing FTP port numbers breaks FTP:One of the things I have been asked is how to change the port numbers that FTP uses. The rationale is that by changing the port numbers, the "bad" people with analyzers will no longer know what ports to monitor, and therefore, passwords and secret files will be safe. Security by obscurity is not security. There are software analyzers that do nothing but scan all packets looking for keywords like PASS (figure 9). A good port scanner will find all open ports, and by analyzing the banner sent when a connection is made, it will recognize that an FTP server is listening on that port.While changing the port does not give you any real security, it does create some real problems. Go back to figure 3 and assume that the firewalls are smart enough to monitor for the PORT and PASV response messages. Typically, these devices only monitor connections using the FTP control port. So, when you change port numbers, they will no longer do this and data connections will fail. The same problem will also occur with NAT and PAT devices. There are probably ways to configure some devices to process messages on other ports, but you have to get your network administrator to do it — assuming you have a device that supports alternative ports. In addition, you may also have some problems specifying the port number in the FTP client. The Windows command line client does not allow you to specify a port number from the "C" prompt (figure 12), but you can do it from the FTP environment using the open command (figure 13).
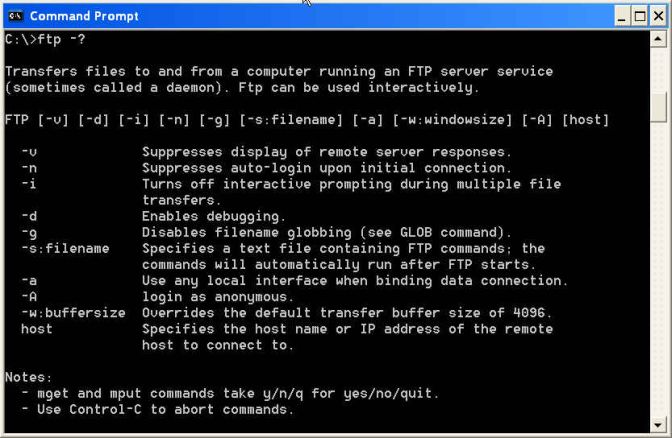 Figure 12: No way to specify an alternate port number from the command line
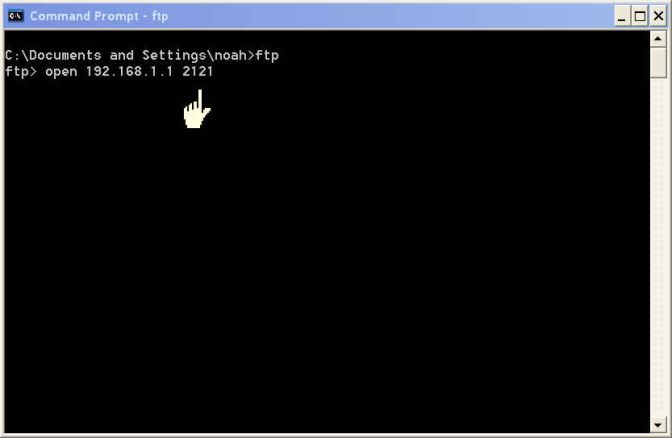 Figure 13: Specifying an alternate port number with the FTP open request The STCP client works the same way. On the command line, you can only enter the host name or IP address of the server, but from the FTP environment, you can issue the open request with both an IP address/host name and a port number. Both the GUI interfaces mentioned make it easy to connect to a server with a non-standard port number (see figures 14 and 15).
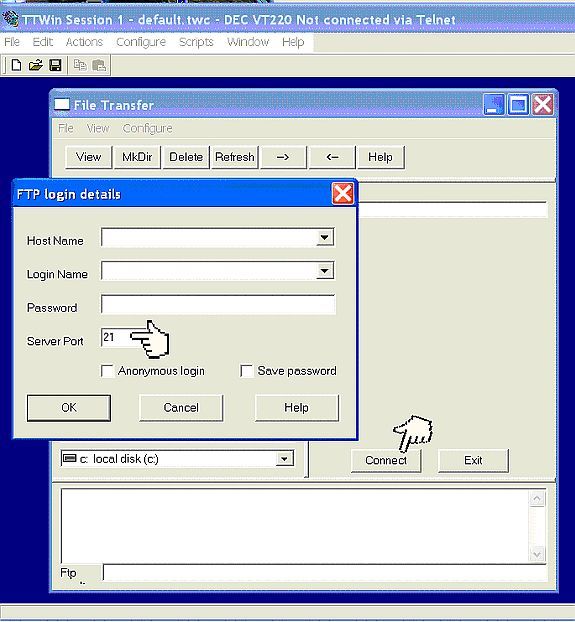 Figure 14: Specifying an alternate port number with TTWin
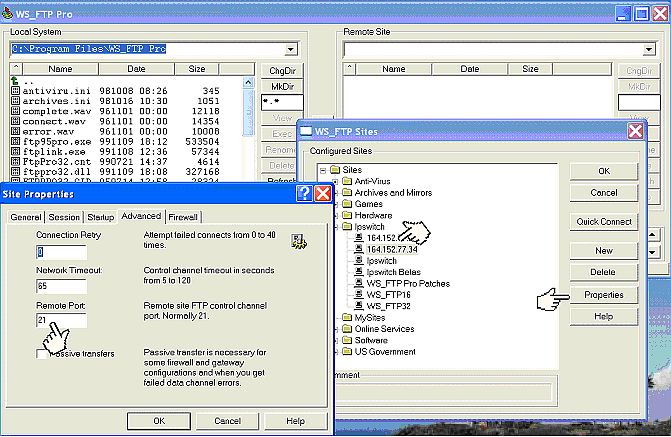 Figure 15: Specifying an alternate port number with WS_FTP Pro OK, if after all this, you still want to change the port numbers, all you need to do is change the FTP entry in the services file (see figure 16).
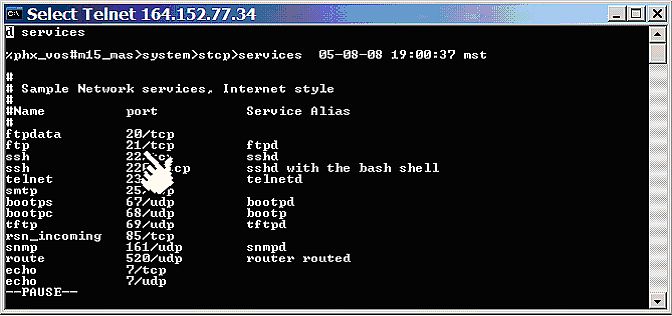 Figure 16: STCP services file Note that even though the ftp-data entry is there, it is not used. The data connection is always one less than the control port. Solutions:We have talked about four problems:
SFTP is part of the OpenSSL/OpenSSH process (Software purchase code S270), which became available in VOS 14.7 (release 1.0) and 15.1+ (release 2.0). It is not available in release 15.0. SFTP uses only one connection from the client to the server. As long as the server's firewall is configured to allow a connection to the SSH server (over port 22), there will be no problems. SFTP can also be used over connections going through a NAT/PAT device and since all data is encrypted using SSL (figure 17), "bad" people with analyzers are mostly out of luck. Note: there are still ways to spy on these connections, specifically with man-in-the-middle attacks, but these types of attacks are not limited to SFTP.
There is a whole host of SFTP clients available for Windows and Unix® operating systems —, just google SFTP. Three Windows-based clients that I have used are psftp, which is a command line tool, WinSCP (figure 18), and SecureFX (figure 19), both of which present GUI interfaces.
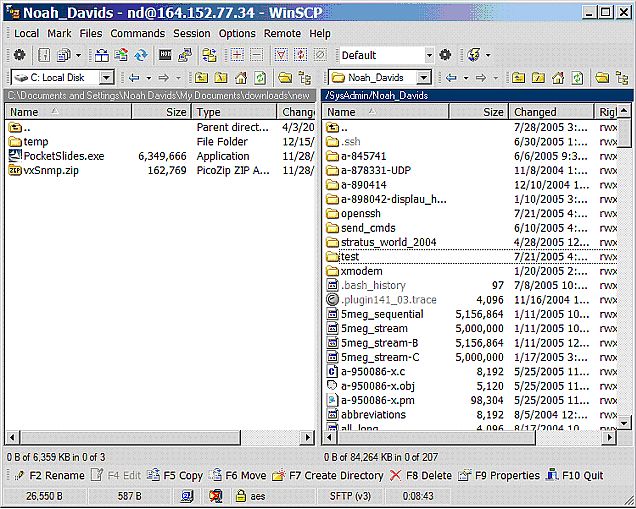 Figure 18 : WinSCP SFTP client
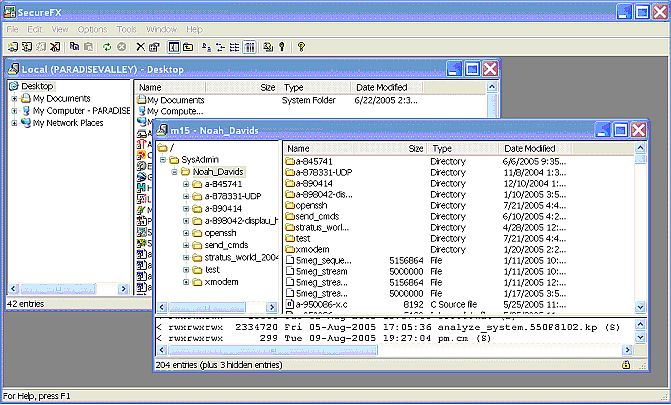 Figure 19: SecureFX SFTP client In addition, the SFTP product for STCP also includes an sftp client (figure 20).
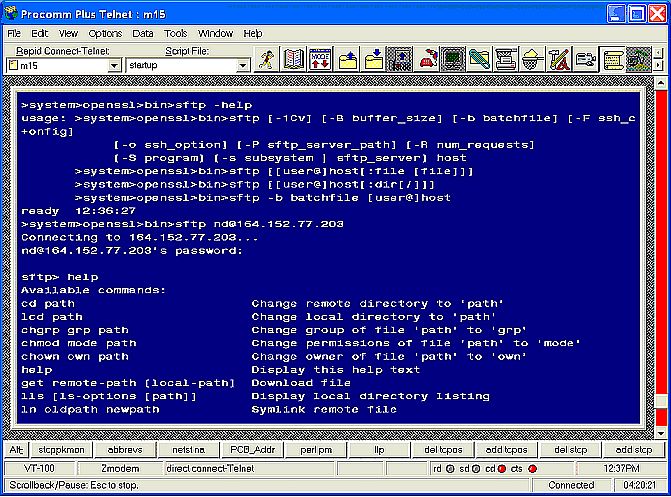 Figure 20: STCP's SFTP client One final note, for those people wondering: yes, the STCP SSH server
allows interactive logins (directly in release 2.0 and via tunneling in
release 1.0) and the STCP SSH client can be used to log into another
system running SSH.
mailto:noah.davids@stratus.com
|